Twitter Feed
Mobile device security: A new frontier for hackers
Recent security breaches have heightened our awareness of cybersecurity issues. The hack and other security breaches have resulted in unprecedented damages. However, the majority of mobile device users have yet to be sensitized…
Learn How To Buy Cloud From GovLoop & ViON
“Government IT managers must accept that cloud computing services are services, not the purchases of technology. This usually represents a fundamental change in how technology is acquired and managed. Since…
A VETS 360 BENEFIT – LATINO FILM INDUSTRY POST OSCAR PARTY
GUESS WHO SUPPORTS VETS 360? You can support them too at the: THE OFFICIAL LATINO FILM INDUSTRY POST OSCAR PARTY The Veterans 360 mission is to support our young combat…
South Asia’s Biggest Tech Event – “Digital World 2015”
I am proud and honored to announce that I have been added as a speaker at SouthAsia’s biggest tech event “Digital World 2015” , 9th – 12th February, 2015 at…
Fear Hackers? First invest in an IT security culture change
by Kevin L.Jackson With all the news these days about cyberterrorism and hacking the cloud may seem like the last place you would want to put your precious information. Pew…
CloudCamp Bangladesh In Dhaka! – February 11, 2015
Did you know that….. Goldman Sachs recognized Bangladesh as one of the Next Eleven (N-11) – a list of eleven countries having strong potential for becoming the world’s largest economies…
Agile is not the absence of ITIL!
by Jodi Kohut ITIL (formerlyknown as the Information Technology Infrastructure Library) has been the best management practices framework of choice for world class IT Operations organizations. The 5 stage framework:…
Cloud Security: Understanding the Cloud Computing Threat Landscape
In the last two years, IT security breaches have hit the White House, the State Department, the top federal intelligence agency, the largest American bank, the top hospital operator, energy…
Federal Cloud Computing Summit on January 14-15, Washington, DC
The Federal Cloud Computing Summit will be held on January 14-15, 2015 at the Marriott Metro Center in Washington, D.C. (Complimentary government and academic registration) This educational symposium will feature cloud computing…
CONGRATULATIONS! Inaugural Cloud Computing Class at Mira Costa College Graduates!!
Anthony Dorrah, Jose Chapman, Mike Chatelain, Lisa Heiden, Ginelle Johnson, Robert Minson, Alfredo Morales We are so proud of the success of out first cloud computing training class. This group…
“A wargame is a game that represents a military operation.”
“Military simulations, also known informally as war games, are simulations in which theories of warfare can be tested and refined without the need for actual hostilities”
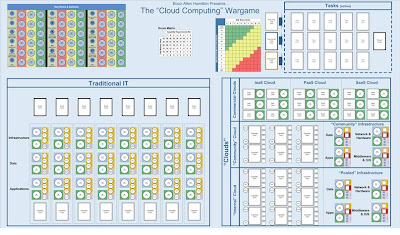 By actively applying modeling and simulation to IT decision making The Cloud Computing Wargame helps players and organizations understand:
By actively applying modeling and simulation to IT decision making The Cloud Computing Wargame helps players and organizations understand:
- The inter-relationships between cloud computing technology and mission requirements
- How long-term cloud computing strategy can develop, evolve, and change.
- The interaction between different activities that occur within an IT organization in order to implement and support IT capabilities in different capabilities matrices.
- How different strategies maximize mission impact and value
- How different roles work with business and IT partners throughout the organization and value chain.
You comments and suggestions are welcome. I look forward to seeing you at FOSE for this exciting unveiling.
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes
