Twitter Feed
Transformation Network
The Achilles heel of every transformative business model is their reliance on ever increasing amounts of data that need to be transported quickly across wide area networks and processed at…
Essential Characteristics of Cloud Computing as Digital Transformation
Hybrid IT blends traditional datacenters, managed service providers, and cloud service providers to deliver the necessary mix of information technology services. This IT consumption model enables a composable infrastructure which…
Transformation Innovation
4 Factors Driving Digital Transformation ROI The critical assessment factors for cloud ROI risk probability are the following: Infrastructure utilization Speed of migration to cloud Ability to scale business/mission processes…
Transformation Frameworks
Digital transformation necessitates changes in an organization’s operational processes. According to Harvard, a focus on operations can lead to business process optimization and entirely new revenue streams. Three common routes…
Transformation Infrastructure
Hybrid IT enables a composable infrastructure which describes a framework whose physical compute, storage, and network fabric resources are treated as services. Resources are logically pooled so that administrators need…
Essential Characteristics of Cloud Computing as Digital Transformation
A survey of 2,000 executives conducted by Cognizant in 2016 identified the top five ways digital transformations generate value: Accelerating speed to market Strengthening competitive positioning Boosting revenue growth Raising…
Embrace Transformation
From a business perspective, differentiating business processes and quality customer service are central to overall success. Business leaders must therefore clearly identify and measure how information technology contributes to the…
Computer Vision Advances Zero-Defect Manufacturing
by Kevin L. Jackson Electronics manufacturers operate in a challenging environment. It’s hard enough to keep up with the ever-accelerating rate of change in the industry. Now customers want increasingly…
Real-Time Analytics Power the Roadway of the Future
By Kevin L. Jackson The complexities of citywide traffic are pushing the limits of existing transportation management systems. Outdated infrastructure is based on proprietary, single-purpose subsystems, making it costly to…
Thriving on the Edge: Developing CSP Edge Computing Strategy
Communications Service Providers (CSPs) are facing significant business model challenges. Referred to generally as edge computing, the possibilities introduced by the blending of 5G networks and distributed cloud computing technologies are…
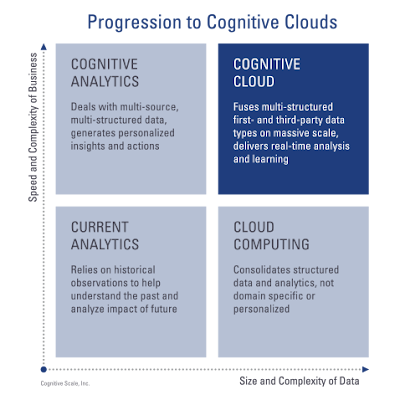
According to the IBM Institute for Business Value the market will see a rapid adoption of initial cognitive systems. The most likely candidates have moved beyond descriptive and diagnostic, predictive and routine industry-specific capabilities. 70 percent of survey respondents are currently using advanced programmatic analytics in three or more departments. In fact, the widespread adoption of cognitive systems and artificial intelligence (AI) across various industries is expected to drive worldwide revenues from nearly US$8.0 billion in 2016 to more than US$47 billion in 2020.
The analyst firm IDC predictsthat the banking, retail, healthcare and discrete manufacturing industries will generate more than 50% of all worldwide cognitive/ AI revenues in 2016. Banking and retail will each deliver nearly US$1.5 billion, while healthcare and discrete manufacturing will deliver the greatest revenue growth over the 2016-2020 forecast period, with CAGRs of 69.3% and 61.4%, respectively. Education and process manufacturing will also experience significant growth over the forecast period.
th’s ability to replicate intuitive experiences provides a number of opportunities within sentiment analysis. With its ability to understand scenes and context, it can decipher how people are feeling based off facial expressions or voice stress levels.
- Need robust and simplified data classification processes in order to more easily deliver industry and business model specific value;
- Require the implementation of information technology security controls that are driven by data value and role based access control paradigms; and
- Leverage software applications that should be developed using ISO 27034 which is a multi-part standard on specifying, designing/selecting and implementing information security controls through a set of processes integrated throughout an organization’s Systems Development Life Cycle/s (SDLC).
( Thank you. If you enjoyed this article, get free updates by email or RSS – © Copyright Kevin L. Jackson 2016)
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes