Twitter Feed
Lynn DeCourcey Showcased in ExecutiveBiz
Kudos to my colleague Lynn DeCourcey for her recent interview on ExecutiveBiz.com! Lynn is NJVC vice president and general manager, cyber security. She oversees all aspects of the company’s cyber…
BISNOW Data Center Event Highlight’s Cloud
A big thank you to BISNOW and my fellow panel members for an outstanding discussion and very informative event, last week’s Data Center Investment Conference and Expo. The federal marketplace…
GSA Seeks Cloud Brokerage Information
GSA is using the RFI process to collect information about alternative models and/or solutions for future cloud acquisition vehicles and processes that further these goals. One emerging concept in cloud…
DoD Cloud Computing Strategy
The DoD recently released the department’s formal cloud computing strategy. DoD Cloud Computing Strategy View more documents from Kevin Jackson. In the forward, DoD CIO Teresa Takai said that: “The…
FedRAMP PMO Releases First Set of 3PAOs
Late today the FedRAMP Program Management Office released the first list of certified Third Party Assessment Organizations (3PAOs). These companies are accredited to perform initial and periodic assessment of cloud…
FedRAMP Releases Updated Security Assessment Plan Templates
Last week the GSA FedRAMP Program Office released the latest version of the cloud computing Security Assessment Plan (SAR) template. This document is the most recent step toward the Federal…
NJVC® and Gravitant® Announce New Strategic Alliance: Partnership to Benefit Federal Agencies with Powerful Provision and Management of Cloud Services that Unify Multiple Providers
Vienna, Va., April 4, 2012 — NJVC®, one of the largest information technology solutions providers supporting the U.S. Department of Defense, and Gravitant®, a provider of cloud brokerage and management…
NJVC® VP and GM, Cloud Services, Kevin L. Jackson to Speak on Cloud Security at 2012 Emerging Threats and Cyber Defense Symposium
Vienna, Va., March 15, 2012 — NJVC®, one of the largest information technology solutions (IT) providers supporting the U.S. Department of Defense, is pleased to announce that Kevin L. Jackson,…
NJVC’s Kevin L. Jackson Co-Authors INSA White Paper on Cloud Computing for the Intelligence Community
Findings Reflect Insight from More than 50 Cloud Thought Leaders VIENNA, Va.–(BUSINESS WIRE)–NJVC®, one of the largest information technology solutions (IT) providers supporting the U.S. Department of Defense, announces…
INSA Study on Cloud Computing in the Intelligence Community: Rollout 13 March 2012 | SYS-CON MEDIA
(Originally posted by Bob Gourley at CTOvision) Over the last year I’ve had the pleasure of serving with a team of volunteers from the Intelligence and National Security Alliance…
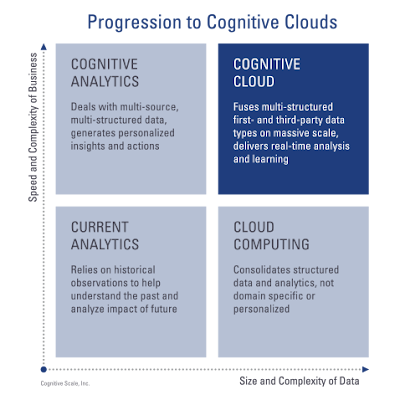
According to the IBM Institute for Business Value the market will see a rapid adoption of initial cognitive systems. The most likely candidates have moved beyond descriptive and diagnostic, predictive and routine industry-specific capabilities. 70 percent of survey respondents are currently using advanced programmatic analytics in three or more departments. In fact, the widespread adoption of cognitive systems and artificial intelligence (AI) across various industries is expected to drive worldwide revenues from nearly US$8.0 billion in 2016 to more than US$47 billion in 2020.
The analyst firm IDC predictsthat the banking, retail, healthcare and discrete manufacturing industries will generate more than 50% of all worldwide cognitive/ AI revenues in 2016. Banking and retail will each deliver nearly US$1.5 billion, while healthcare and discrete manufacturing will deliver the greatest revenue growth over the 2016-2020 forecast period, with CAGRs of 69.3% and 61.4%, respectively. Education and process manufacturing will also experience significant growth over the forecast period.
th’s ability to replicate intuitive experiences provides a number of opportunities within sentiment analysis. With its ability to understand scenes and context, it can decipher how people are feeling based off facial expressions or voice stress levels.
- Need robust and simplified data classification processes in order to more easily deliver industry and business model specific value;
- Require the implementation of information technology security controls that are driven by data value and role based access control paradigms; and
- Leverage software applications that should be developed using ISO 27034 which is a multi-part standard on specifying, designing/selecting and implementing information security controls through a set of processes integrated throughout an organization’s Systems Development Life Cycle/s (SDLC).
( Thank you. If you enjoyed this article, get free updates by email or RSS – © Copyright Kevin L. Jackson 2016)
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes