Twitter Feed
SourceConnecte! Marketplace With A Mission
Earlier this year, GC GlobalNet launched a new breed of B2B e-commerce sites. Curated by Kevin L. Jackson, SourceConnecte (with an “eâ€) went live with three strategic goals in mind: Efficiently leverage modern…
Potential vs. Reality: Is Edge Computing Real?
Edge computing provides compute, storage, and networking resources close to devices generating traffic. Its benefits are based on an ability to provide new services capable of meeting stringent operational requirements…
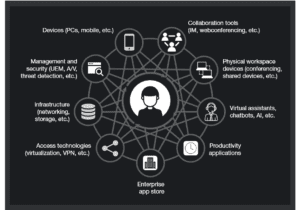
Enabling Digital Transformation
Digital transformation integrates technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing products and services to a global…
The ThinkShield Story Part 1: The Challenge
The cybersecurity challenge seems to be growing daily. Threats are becoming more sophisticated, and attacks are becoming more destructive while the corporate world’s response seems to resemble a deer…
CIO dream team: Who’s in and why?
Today’s CIO navigates the twin challenges of enabling new business models and managing rapid technological change. Cloud computing strategies are now table stakes. CIOs must make complex decisions about using…
Digital Transformation and the Mainframe
Digital transformation infuses digital technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing digital products and services to…
Composable Architecture Q&A. Are you ready?
Q: Is it time for my company to jump on the composable architecture bandwagon? A: Composable architectures are quickly becoming essential to the modern enterprise. Citing a recent Forrester study:…
Increase Productivity by Reducing Technology Distraction: Lessons from Forrester Research
Workplace productivity is hurt every day by the very technology developed and purchased to improve it. Forrester announced this surprising conclusion in their latest “How To Wake Up From The Nightmare…
Unveiling the end-to-end capabilities for the networked society
An Interview with Henrik Basilier By Kevin L. Jackson The telecom industry is rapidly moving towards a future in which networks must have the capabilities of delivering services with the…
AT&T Finance Solutions GM on Shrimping, Software, and CX
Helping clients address the trends and challenges presented by the Financial Services industry is the main focus for René Dufrene in his role as General Manager of Finance Solutions at…
Over the past years, government cloud computing has steadily moved forward from it’s early beginnings as an interesting curiosity:
Since Sunday’s broadcast, I’ve been asked numerous times about my real answer to the question “Will ‘Cloud Computing’ Work In White House“. Although I would never assume to be in a position to advise the President-elect, I’m more than happy, however, to add my voice to the Center for Strategic and International Studies (CSIS) and the distinguished list of contributors that recently released the CSIS Commission on Cybersecurity for the 44th Presidency.
I truly believe that cloud computing technology can be used to implement some of their recommendations. One in particular is their recommendation for a National Office for Cyberspace (NOC) and a new National Security Council Cybersecurity Directorate (NSCCD). Along with the relevant agencies, these organizations would:
“Assume expanded authorities, including revised Federal Information Security management Act (FISMA) authorities, oversight of the Trusted Internet Connections (TIC) initiative, responsibility for the Federal Desktop Core Configuration (FDCC) and acquisition reform, and the ability to require agencies to submit budget proposals relating to cyberspace to receive its approval prior to submission to OMB.”
Government cloud computing is a reality and as Peter Mell of NIST succinctly put it, “2010 will be the year of the cloud computing pilot.” I look forward to continuing this exciting conversation with you all!
2011 will be the breakout year for GovCloud! Pressure to reduce budget, pressure to manage I resources better and the political pressure of the next presidential election will combine to accelerate adoption. The GSA IaaS groundwork has been laid and new policies are just about ready to be released !!
December 2011: And what did Santa bring this year!!
Each Executive department or agency shall:
i. Use FedRAMP when conducting risk assessments, security authorizations, and granting ATOs for all Executive department or agency use of cloud services;
ii. Use the FedRAMP PMO process and the JAB-approved FedRAMP security authorization requirements as a baseline when initiating, reviewing, granting and revoking security authorizations for cloud services;
iii. Ensure applicable contracts appropriately require CSPs to comply with FedRAMP
security authorization requirements;
“PERFORMANCE PLAN FOR REDUCTION OF RESOURCES
REQUIRED FOR DATA SERVERS AND CENTERS.— …
(2) DEFENSE-WIDE PLAN.—
(A) IN GENERAL.—Not later than April 1, 2012, the Chief Information Officer of the Department shall submit to the congressional defense committees a performance plan for a reduction in the resources required for data centers and information systems technologies Department-wide. The plan shall be based upon and incorporate appropriate elements of the plans submitted under paragraph (1).
(B) ELEMENTS.—The performance plan required under this paragraph shall include the following:
(ii) A Department-wide strategy for each of the following: ….
(II) Transitioning to cloud computing.
(III) Migration of Defense data and government-provided services from Department-owned and operated data centers to cloud computing services generally available within the private sector that provide a better capability at a lower cost with the same or greater degree of security.
(IV) Utilization of private sector-managed security services for data centers and cloud computing services.”
Happy Holidays to All !!!

( Thank you. If you enjoyed this article, get free updates by email or RSS – KLJ )
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes