Twitter Feed
SourceConnecte! Marketplace With A Mission
Earlier this year, GC GlobalNet launched a new breed of B2B e-commerce sites. Curated by Kevin L. Jackson, SourceConnecte (with an “eâ€) went live with three strategic goals in mind: Efficiently leverage modern…
Potential vs. Reality: Is Edge Computing Real?
Edge computing provides compute, storage, and networking resources close to devices generating traffic. Its benefits are based on an ability to provide new services capable of meeting stringent operational requirements…
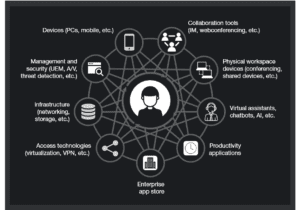
Enabling Digital Transformation
Digital transformation integrates technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing products and services to a global…
The ThinkShield Story Part 1: The Challenge
The cybersecurity challenge seems to be growing daily. Threats are becoming more sophisticated, and attacks are becoming more destructive while the corporate world’s response seems to resemble a deer…
CIO dream team: Who’s in and why?
Today’s CIO navigates the twin challenges of enabling new business models and managing rapid technological change. Cloud computing strategies are now table stakes. CIOs must make complex decisions about using…
Digital Transformation and the Mainframe
Digital transformation infuses digital technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing digital products and services to…
Composable Architecture Q&A. Are you ready?
Q: Is it time for my company to jump on the composable architecture bandwagon? A: Composable architectures are quickly becoming essential to the modern enterprise. Citing a recent Forrester study:…
Increase Productivity by Reducing Technology Distraction: Lessons from Forrester Research
Workplace productivity is hurt every day by the very technology developed and purchased to improve it. Forrester announced this surprising conclusion in their latest “How To Wake Up From The Nightmare…
Unveiling the end-to-end capabilities for the networked society
An Interview with Henrik Basilier By Kevin L. Jackson The telecom industry is rapidly moving towards a future in which networks must have the capabilities of delivering services with the…
AT&T Finance Solutions GM on Shrimping, Software, and CX
Helping clients address the trends and challenges presented by the Financial Services industry is the main focus for René Dufrene in his role as General Manager of Finance Solutions at…
As fellow blogger Reuven Cohen mentions in his post, Federal cloud computing is indeed heating up:
- Vivek Kundra held a US Federal Government Cloud Computing Summit yesterday
- The Federal CIO Council is officially studying effective uses of cloud computing
- According to Network World, an INPUT study places Federal spend on cloud services at $277M in 2008 growing to $793M by 2013
- Patrick Stingley has been named as the CTO, Federal Cloud for GSA
- NIST has reveled their draft definition of cloud computing (see below)
—————————————————————————————-
Draft NIST Working Definition of Cloud Computing
4-24-09
Peter Mell and Tim Grance – National Institute of Standards and Technology, Information Technology Laboratory
Note 1: Cloud computing is still an evolving paradigm. Its definitions, use cases, underlying technologies, issues, risks, and benefits will be refined in a spirited debate by the public and private sectors. These definitions, attributes, and characteristics will evolve and change over time.
Note 2: The cloud computing industry represents a large ecosystem of many models, vendors, and market niches. This definition attempts to encompass all of the various cloud approaches.
Definition of Cloud Computing:
Cloud computing is a pay-per-use model for enabling available, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. This cloud model promotes availability and is comprised of five key characteristics, three delivery models, and four deployment models.
Key Characteristics:
- On-demand self-service. A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed without requiring human interaction with each service’s provider.
- Ubiquitous network access. Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, laptops, and PDAs).
- Location independent resource pooling. The provider’s computing resources are pooled to serve all consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. The customer generally has no control or knowledge over the exact location of the provided resources. Examples of resources include storage, processing, memory, network bandwidth, and virtual machines.
- Rapid elasticity. Capabilities can be rapidly and elastically provisioned to quickly scale up and rapidly released to quickly scale down. To the consumer, the capabilities available for rent often appear to be infinite and can be purchased in any quantity at any time.
- Pay per use. Capabilities are charged using a metered, fee-for-service, or advertising based billing model to promote optimization of resource use. Examples are measuring the storage, bandwidth, and computing resources consumed and charging for the number of active user accounts per month. Clouds within an organization accrue cost between business units and may or may not use actual currency.
Note: Cloud software takes full advantage of the cloud paradigm by being service oriented with a focus on statelessness, low coupling, modularity, and semantic interoperability.
Delivery Models:
- Cloud Software as a Service (SaaS). The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure and accessible from various client devices through a thin client interface such as a Web browser (e.g., web-based email). The consumer does not manage or control the underlying cloud infrastructure, network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user-specific application configuration settings.
- Cloud Platform as a Service (PaaS). The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created applications using programming languages and tools supported by the provider (e.g., java, python, .Net). The consumer does not manage or control the underlying cloud infrastructure, network, servers, operating systems, or storage, but the consumer has control over the deployed applications and possibly application hosting environment configurations.
- Cloud Infrastructure as a Service (IaaS). The capability provided to the consumer is to rent processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, deployed applications, and possibly select networking components (e.g., firewalls, load balancers).
Deployment Models:
- Private cloud. The cloud infrastructure is owned or leased by a single organization and is operated solely for that organization.
- Community cloud. The cloud infrastructure is shared by several organizations and supports a specific community that has shared concerns (e.g., mission, security requirements, policy, and compliance considerations).
- Public cloud. The cloud infrastructure is owned by an organization selling cloud services to the general public or to a large industry group.
- Hybrid cloud. The cloud infrastructure is a composition of two or more clouds (internal, community, or public) that remain unique entities but are bound together by standardized or proprietary technology that enables data and application portability (e.g., cloud bursting).
Each deployment model instance has one of two types: internal or external. Internal clouds reside within an organizations network security perimeter and external clouds reside outside the same perimeter.
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes