Twitter Feed
SourceConnecte! Marketplace With A Mission
Earlier this year, GC GlobalNet launched a new breed of B2B e-commerce sites. Curated by Kevin L. Jackson, SourceConnecte (with an “eâ€) went live with three strategic goals in mind: Efficiently leverage modern…
Potential vs. Reality: Is Edge Computing Real?
Edge computing provides compute, storage, and networking resources close to devices generating traffic. Its benefits are based on an ability to provide new services capable of meeting stringent operational requirements…
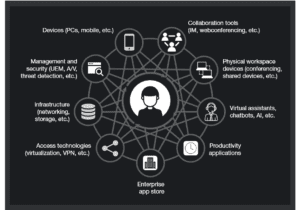
Enabling Digital Transformation
Digital transformation integrates technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing products and services to a global…
The ThinkShield Story Part 1: The Challenge
The cybersecurity challenge seems to be growing daily. Threats are becoming more sophisticated, and attacks are becoming more destructive while the corporate world’s response seems to resemble a deer…
CIO dream team: Who’s in and why?
Today’s CIO navigates the twin challenges of enabling new business models and managing rapid technological change. Cloud computing strategies are now table stakes. CIOs must make complex decisions about using…
Digital Transformation and the Mainframe
Digital transformation infuses digital technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing digital products and services to…
Composable Architecture Q&A. Are you ready?
Q: Is it time for my company to jump on the composable architecture bandwagon? A: Composable architectures are quickly becoming essential to the modern enterprise. Citing a recent Forrester study:…
Increase Productivity by Reducing Technology Distraction: Lessons from Forrester Research
Workplace productivity is hurt every day by the very technology developed and purchased to improve it. Forrester announced this surprising conclusion in their latest “How To Wake Up From The Nightmare…
Unveiling the end-to-end capabilities for the networked society
An Interview with Henrik Basilier By Kevin L. Jackson The telecom industry is rapidly moving towards a future in which networks must have the capabilities of delivering services with the…
AT&T Finance Solutions GM on Shrimping, Software, and CX
Helping clients address the trends and challenges presented by the Financial Services industry is the main focus for René Dufrene in his role as General Manager of Finance Solutions at…
(This is part 4 of the series entitled “Implementation of Cloud Computing Solutions in Federal Agencies”. First published on Forbes.com, this series provides the content of a whitepaper I recently authored. A copy of the complete whitepaper will be available at NJVC.com starting September 7, 2011.)
The defense and intelligence communities are not immune to cloud computing. Arguably more than any other government agencies, their missions require a fabric of utility computing that scales on demand and enables self discovery and self-service access to secure, timely and relevant information in support of mission: individual or shared. The traditional IT model requires system engineering that binds most software to the hardware and does not provide an enterprise suite of functionality or allow for increased flexibility and a governed lifecycle of services. Designing software independence from the hardware allows an operating system, applications and data to “live” across the enterprise and is fundamental to the transformation of compute, storage and network functionality.
Defense is dealing with a $78 billion budget cut—the first since September 11, 2001—and another $100 billion in other cost-cutting measures over a five-year period commencing in FY 2012. Defense Secretary Robert Gates is directing that the budget be cut from agency administrative and structural areas (e.g., the Office of the Assistant Secretary of Defense for Network Intelligence and Information, the Business Transformation Agency, and the Joint Forces Command are in the process of being eliminated or disestablished with some essential functions transferred to other organizations with the Pentagon).
In an official statement on the proposed budget costs provided on January 6, 2011, Secretary Gates said: “First, reforming how the department uses information technology, which costs us about $37 billion a year. At this time all of our bases and headquarters have their own separate IT infrastructure and processes, which drive up costs and create cyber vulnerabilities. The department is planning to consolidate hundreds of data centers and move to a more secure enterprise system, which we estimate could save more than $1 billion a year.” Department of Defense Chief Information Officer Terry Takai also publically commented about the potential IT budget cuts at an April 21, 2011, INPUT event. Takai commented on DoD’s support of the move of some of its IT operations to the cloud—particularly data centers.
Cloud Computing and Mission Support
Information is often the decisive discriminator in modern conflict. Studies of recent mission failures highlighted this fact, finding that many of these failures were caused by:
- Existence of data silos
- Human-based document exploitation process
- Reliance on “operationally proven” processes and filters typically used to address the lack of computational power or decision time
Also disturbing is that in most of these cases, the critical piece of information necessary for mission was in possession. The failure wasn’t in obtaining the information, but in locating and applying it to the mission at hand. Cloud computing uniquely addresses all of these important issues.
Data silos evolved from a system-centric IT proc urement policy and an almost reflexive reliance onrelational database technology. In developing early data processing systems, the high cost of memory and storage led to a premium being placed on the efficiency of application data access and retrieval. Relational database technology effectively addressed this need, which in turn led to its pervasive use across government. In modern IT system development, memory and storage are cheap—and getting cheaper—which has led to internet-scale storage and search paradigms that are the stuff of everyday use today. The world’s largest databases cannot, in fact, be searched quickly using a relational database management approach. Today’s ability to search multi-petabyte data stores in milliseconds virtually eliminates the need for data silos. This capability is realized in cloud-based storage. Documents are the persistent records of human activity. As such, they are used to provide insight into the societal structure and processes of our opponents. Conflict, however, is entity and event centric. The intelligence professional must, therefore, interpret documents and translate that data into operationally relevant entities and events. The time and resource intensive nature of this skillcraft is perfectly suited for the precision search and analytic capabilities of the modern compute cloud. The use of highly standardized and virtualized commodity infrastructure, not only make the automation of this function possible, but it enables real-time continuous processing of the now digital document flow of our adversaries. This commodity also removes the human from this tedious task, allowing intelligence professionals to apply higher order professional analysis and insight.
The human-based document exploitation process led directly to an institutional reliance on the aforementioned “operationally proven” processes and filters. Instantiated by the use of multi-page structure query language and the ubiquitous goal of obtaining an appropriate “working set” of data, these time-honored processes were born from the need to meet critical decision timelines within a computationally inadequate environment. Cloud techniques and technologies can now be used to work on all the data. And with an ability to leverage the power of a supercomputer at will, the working set requirement is now an anachronism and critical decision timelines can now be more easily met.
Cloud computing is unique in its ability to address these critical defense and intelligence mission needs. That’s why cloud computing is critical to our national defense. As a bonus, cloud computing offers defense and intelligence agencies the ability to increase efficiencies and incur marked cost savings during their lifecycles to alleviate some of the pressure of budget reductions. Moving IT operations to the cloud also will assist in enhanced collaboration.


( Thank you. If you enjoyed this article, get free updates by email or RSS – KLJ )
2 Comments
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes












Thanks for the experiment. It was very informative and useful. I keep in mind. Thanks a lot for sharing such a awe-some information.
Android app developer| Android apps development|
Cloud computing is really an interesting part to know and learn about. U have made an interesting post.
Free Ecommerce Software | Web Shopping Cart