Twitter Feed
SourceConnecte! Marketplace With A Mission
Earlier this year, GC GlobalNet launched a new breed of B2B e-commerce sites. Curated by Kevin L. Jackson, SourceConnecte (with an “eâ€) went live with three strategic goals in mind: Efficiently leverage modern…
Potential vs. Reality: Is Edge Computing Real?
Edge computing provides compute, storage, and networking resources close to devices generating traffic. Its benefits are based on an ability to provide new services capable of meeting stringent operational requirements…
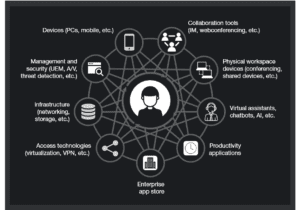
Enabling Digital Transformation
Digital transformation integrates technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing products and services to a global…
The ThinkShield Story Part 1: The Challenge
The cybersecurity challenge seems to be growing daily. Threats are becoming more sophisticated, and attacks are becoming more destructive while the corporate world’s response seems to resemble a deer…
CIO dream team: Who’s in and why?
Today’s CIO navigates the twin challenges of enabling new business models and managing rapid technological change. Cloud computing strategies are now table stakes. CIOs must make complex decisions about using…
Digital Transformation and the Mainframe
Digital transformation infuses digital technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing digital products and services to…
Composable Architecture Q&A. Are you ready?
Q: Is it time for my company to jump on the composable architecture bandwagon? A: Composable architectures are quickly becoming essential to the modern enterprise. Citing a recent Forrester study:…
Increase Productivity by Reducing Technology Distraction: Lessons from Forrester Research
Workplace productivity is hurt every day by the very technology developed and purchased to improve it. Forrester announced this surprising conclusion in their latest “How To Wake Up From The Nightmare…
Unveiling the end-to-end capabilities for the networked society
An Interview with Henrik Basilier By Kevin L. Jackson The telecom industry is rapidly moving towards a future in which networks must have the capabilities of delivering services with the…
AT&T Finance Solutions GM on Shrimping, Software, and CX
Helping clients address the trends and challenges presented by the Financial Services industry is the main focus for René Dufrene in his role as General Manager of Finance Solutions at…
| Carmen Krueger, SAP NS2 SVP & GM |
While SAP is globally renowned as a provider of enterprise management software, the name is hardly ever associated with the spooky world of intelligence. That is one reason why I jumped at the opportunity to talk with SAP executives responsible for the company’s work in that clandestine marketplace.
 |
| Hunter Downey, NS2 Cloud Solution Director |
( This content is being syndicated through multiple channels. The opinions expressed are solely those of the author and do not represent the views of GovCloud Network, GovCloud Network Partners or any other corporation or organization.)
( Thank you. If you enjoyed this article, get free updates by email or RSS – © Copyright Kevin L. Jackson 2015)
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes