Twitter Feed
Cloud Computing Evolves: An Interview with Mats Johansson
Recently, Ericsson Digital released an amazing report on Edge Computing and 5G. In it, they explained how distributed cloud computing is paving the way for the future of network communications. They…
The IoT Nexus: Bosch Connected World 2019 in Berlin
Next week, I will be influencing #LikeABosch as I accept an invitation from the company to attend Bosch ConnectedWorld 2019 (BCW19) in Berlin, Germany. This is one of the world’s largest international…
Survive and Thrive With Digital Transformation
First cloud computing then multi-cloud. How can we get ahead of this digital transformation nightmare? These are the laments heard in conference rooms and board meeting around the world. While…
The “George Jetson” of Today
He grew up in Silicon Valley, landed his first job at Apple Computers, was introduced to Nobel Prize winners by his dad and today, he takes a self-driving car…
MWC19: Where Telecommunications and Cloud Meet
As a cloud solution architect, my passion is learning the details about how cloud computing uniquely supports specific business cases. This curiosity is what drove my excitement when Ericsson invited…
Tulane University SoPA Selects “Architechting Cloud Computing Solutions”
Last week, Packt Publishing announced that “Architecting Cloud Computing Solutions” by Kevin L. Jackson and Scott Goessling was selected for use by the Tulane University School of Professional Advancement, Applied Computing Systems & Technology Program as the textbook for…
5G Wireless Technology Connecting Healthcare
Healthcare is in the middle of massive change. Called digital transformation by many, this term describes the industry’s pursuit of the many promises offered by connected patients, connected caregivers, and…
Maria Lensing: The Network Platform for Healthcare’s Future
As a girl, Maria and her family traveled to Memphis, Tennessee to get cancer treatment for her sick brother. The miracle she observed, as the healthcare providers saved her brother’s…
How “Big Iron” Does “Big Regulation”
According to Verizon, there were over there were over 53,000 security incidents in 2017, with over 2,200 of those identified as confirm data breaches. A Ponemon Institute study also showed…
Mainframe Synergies for Digital Transformation
In July of 2018, Broadcom announced its intentions to acquire CA Technologies. In the press release, Hock Tan, President and Chief Executive Officer of Broadcom, said: “This transaction represents an…
If I were a betting man, I’d say that this attack was done using Multi-Stage BGP & DNS Attack Vector. My only real proof is a little common sense as well as the simple reason that a typical HTTP denial of service attack causes a spike in traffic not a drop as illustrated below.

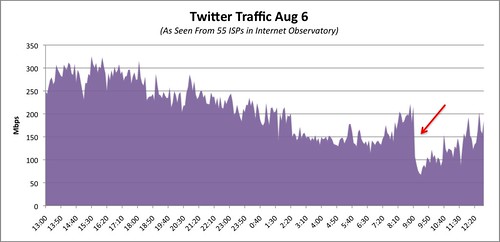
( Thank you. If you enjoyed this article, get free updates by email or RSS – KLJ )
1 Comments
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes











This is so sad.