Twitter Feed
SourceConnecte! Marketplace With A Mission
Earlier this year, GC GlobalNet launched a new breed of B2B e-commerce sites. Curated by Kevin L. Jackson, SourceConnecte (with an “eâ€) went live with three strategic goals in mind: Efficiently leverage modern…
Potential vs. Reality: Is Edge Computing Real?
Edge computing provides compute, storage, and networking resources close to devices generating traffic. Its benefits are based on an ability to provide new services capable of meeting stringent operational requirements…
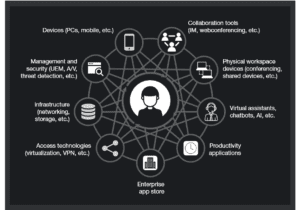
Enabling Digital Transformation
Digital transformation integrates technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing products and services to a global…
The ThinkShield Story Part 1: The Challenge
The cybersecurity challenge seems to be growing daily. Threats are becoming more sophisticated, and attacks are becoming more destructive while the corporate world’s response seems to resemble a deer…
CIO dream team: Who’s in and why?
Today’s CIO navigates the twin challenges of enabling new business models and managing rapid technological change. Cloud computing strategies are now table stakes. CIOs must make complex decisions about using…
Digital Transformation and the Mainframe
Digital transformation infuses digital technology into all areas of an organization’s business or mission. Its fundamental purpose is to create and deliver innovative and industry-changing digital products and services to…
Composable Architecture Q&A. Are you ready?
Q: Is it time for my company to jump on the composable architecture bandwagon? A: Composable architectures are quickly becoming essential to the modern enterprise. Citing a recent Forrester study:…
Increase Productivity by Reducing Technology Distraction: Lessons from Forrester Research
Workplace productivity is hurt every day by the very technology developed and purchased to improve it. Forrester announced this surprising conclusion in their latest “How To Wake Up From The Nightmare…
Unveiling the end-to-end capabilities for the networked society
An Interview with Henrik Basilier By Kevin L. Jackson The telecom industry is rapidly moving towards a future in which networks must have the capabilities of delivering services with the…
AT&T Finance Solutions GM on Shrimping, Software, and CX
Helping clients address the trends and challenges presented by the Financial Services industry is the main focus for René Dufrene in his role as General Manager of Finance Solutions at…
A few weeks ago in an article title “Why the Cloud? Processing, Exploitation and Dissemination“, I described two instances where the newspaper industry used cloud computing in order to process, exploit and disseminate information. In that article I postulated that this is one reason why the intelligence community is interested in cloud computing.
Well Signal Magazine has recently highlighted a specific program where the DoD could use a similar approach. In a project called Valiant Angel, the Joint Intelligence Laboratory, located at the U.S. Joint Forces Command in Norfolk, Virginia, is working on a way for commanders to handle massive amounts of full-motion video being provided from unmanned platforms.
In addition to storing, moving, communicating and accessing large amounts of data, Valiant Angel is also addressing full-motion video processing, exploitation and dissemination (PED). Col. Chuck Mehle II, USA, commander of the Joint Transformation Command for Intelligence (JTC-I), JFCOM, notes that this aspect of full-motion video management is important because currently different people have different meanings for PED.
“For some, PED might be sticking yellow stickies on a screen after the event happens, and then taking notes about it as the video is displayed to them. But Valiant Angel gives them the capability—the John Madden-type capability—to drop the icon onto that video frame. Let’s say there is an event such as an IED [improvised explosive device] placement or an IED detonation or defusing. Immediately across the Defense Department, intelligence enterprise alerts will go out to those people who subscribe to that type of event, that geographic region, that timeframe, you name it,” he explains.
Such a requirement is perfect for cloud computing. An ability to meet surge storage and computing requirements by securely scaling into a on-demand cloud computing infrastructure could actually make projects like Valiant Angel affordable. Since it would be costly and impractical to buy the equipment needed to meet all possible tactical situations, a platform with an inherent ability to expand into a commercially provided cloud infrastructure could be ideal. It’s very difficult to predict real-time tactical processing, exploitation and dissemination requirements. Cloud computing approaches could definitely provide a better option.
5 Comments
Cloud Computing
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- Route1 Announces Q2 2019 Financial Results
- CPUcoin Expands CPU/GPU Power Sharing with Cudo Ventures Enterprise Network Partnership
- ChannelAdvisor to Present at the D.A. Davidson 18th Annual Technology Conference
Cybersecurity
- Route1 Announces Q2 2019 Financial Results
- FIRST US BANCSHARES, INC. DECLARES CASH DIVIDEND
- Business Continuity Management Planning Solution Market is Expected to Grow ~ US$ 1.6 Bn by the end of 2029 - PMR
- Atos delivers Quantum-Learning-as-a-Service to Xofia to enable artificial intelligence solutions
- New Ares IoT Botnet discovered on Android OS based Set-Top Boxes










^^Thanks!!
徵徵徵婚前徵信徵婚姻感情徵大陸抓姦徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵外遇抓姦法律諮詢家暴徵婚前徵信尋人感情挽回大陸抓姦離婚徵徵工商徵信徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵婚前徵信外遇抓姦感情挽回尋人大陸抓姦離婚家暴徵徵工商徵信法律諮詢徵徵徵跟蹤徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵工商徵信徵徵婚前徵信感情挽回外遇抓姦法律諮詢家暴尋人大陸抓姦離婚徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵大陸抓姦徵外遇徵徵徵尋人徵徵家暴徵徵徵徵徵徵徵徵徵工商徵信法律諮詢家暴感情挽回大陸抓姦外遇婚前徵信離婚徵徵尋人徵徵徵徵徵徵徵徵徵徵徵徵工商徵信徵徵徵徵徵徵外遇抓姦法律諮詢家暴婚前徵信大陸抓姦尋人感情挽回徵徵徵徵徵徵徵徵徵徵外遇抓姦婚前徵信感情挽回尋人大陸抓姦工商徵信法律諮詢離婚家暴徵徵徵徵徵徵徵徵徵徵徵徵徵徵工商徵信外遇抓姦法律諮詢家暴婚前徵信尋人感情挽回大陸抓姦離婚徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵婚前徵信工商徵信外遇抓姦尋人離婚家暴大陸抓姦感情挽回法律諮詢徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵離婚感情挽回婚前徵信外遇抓姦家暴尋人徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵工商徵信外遇抓姦法律諮詢家暴婚前徵信尋人感情挽回">徵大陸抓姦離婚徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵婚前徵信工商徵信外遇抓姦尋人離婚家暴大陸抓姦感情挽回法律諮詢徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵徵
But Valiant Angel doesn’t have this capability! It’s based on Isilon — at best it does fast ftp of files and has no distributed processing capability beyond what’s available at a single site.
That’s my point! Valiant Angel could probably does much more with a lot less cost if they would leverage a cloud computing infrastructure something like Animoto. See http://kevinljackson.blogspot.com/2008/12/animoto-automated-imagery-ped.html
Do you have any idea how limited bandwidth is in a combat enviroment? How well does cloud computing work in a high latency, low bandwidth infrastructure?
During the US Navy Trident Warrior exercise, we've been testing the use of Amazon Web Services over simulated shipboard communications systems and have found the use of cloud computing technologies to be very feasible. These test simulated the high latency, low bandwidth environment found shipboard.